Tutanota now comes with dedicated desktop clients
- Connecting to a remote Mac system from a Windows OS can be complicated. The VNC Viewer in the Dameware Remote Support (DRS) software’s Remote Connect dialog makes it easy to connect from Windows OS to Mac OS X and send keyboard and mouse inputs remotely from one computer to the other. Use VNC Viewer to remotely control Mac computers, see exactly what is on the end-user’s screen,.
- Win-acme is a ACMEv2 client for Windows that aims to be very simple to start with, but powerful enough to grow into almost every scenario.
Today we are releasing the first secure desktop clients with built-in encryption for Linux, Windows, Mac OS. This is one of the mostimportant updates since we have first published our secure email service with automatic encryption in March 2014.The new Tutanota desktop clients enable you to use Tutanota directly from your computer without the need of a browser.
Let's Encrypt is a free, automated, and open certificate authority brought to you by the nonprofit Internet Security Research Group (ISRG). 548 Market St, PMB 57274, San Francisco, CA, USA.
Install the secure desktop clients via these links:
- Find more details on the new desktop clients in our How-to.
Improved security by signing applications
The Tutanota desktop applications for Linux, Windows, and Max OS are signed.You can verify the signature here.The signatures makesure that the desktop clients as well as any updates come directly from us and have not been tampered with.
The client validates the signature before installing any update. This reduces the risk of man-in-the-middle attackseven further as a potential attacker would haveto change not only the client on our server, but also the key, which we publish so people can verify that the keys match.
The code for our desktop clients is published on GitHub as open source, just as the code for our webmail cient andour Android and iOS apps. At Tutanota we believe that using free software is the best way to guarantee maximum security.
Read here why our Google-free Android app makes Tutanota one of the best for open source emails.
Secure desktop clients based on Electron
When we decided to build desktop clients for Tutanota, we carefully evaluated whether to build a native client foreach OS or use Electron to convert our webmail client into desktop clients for Linux, Windows and Mac OS. We haveopted to use Electron for the following reasons:
- We are able to support all three major operating systems with minimum effort.
- We can quickly adapt the new desktop clients so that they match new features added to the webmail client.
- We can allocate development time to particular desktop features, e.g. offline availablity, email import, thatwill simultaneously be available in all three desktop clients.
Native desktop clients have a slight advantage towards clients built with Electron in regards to RAM, but thisadvantage does not outweigh the fact that with Electron we can support all three operating systems with miminumdevelopment effort. On top of that, we have put special attention to this issue when redesigning our new webmailclient in 2017 and 2018 so that the current desktop versions of Tutanota need relatively little RAM.
At Tutanota we are a small team so we have to focus on how to develop the best product with miminum effort, andElectron enables us to achieve just that.
Please note that if you open several instancesof the desktop client, only the instance that has been opened first saves data if you choose to save the loginpassword or create a search index. At the moment, the additional instances only use a temporary cacheso that such data is not saved when you close the desktop client again.
After releasing the first basic version, wewill now focus on adding typical desktop features to the clients.
Email import and synchronization with external mailboxes
Let's Encrypt Client Certificate
The next feature on our development roadmap for the desktop clients is email import and synchronization with externalmailboxes. The import feature via the Tutanota desktop clients will enable Tutanota to import emails from external mailboxesand encrypt the data locally on your device before storing it on the Tutanota servers.
This feature is very important to us as it will let you import and encrypt external data in Tutanota without our serversever being able to see or read your data.
The Tutanota webmail client does not support such an import feature because with the webmail version it is impossible to encryptimported data before it hits the server.
Offline availability with the desktop clients
The desktop clients also give us the possibility to add offline support to Tutanota. In the future, you will beable to access and view your encrypted mailbox even when you have no access to the Internet via our dedicated desktop clients.
Perfect email alternative to privacy-invading services
To provide the best privacy-focused email service, we are taking every step of your email usage intoaccount. We are never making a trade-off when it comes to security while focusing on your convenience and ease-of-use.
The combination of security with ease-of-use is the reason for Tutanota's continuous growth as well as for thesteadily growing number of end-to-end encrypted emails sent by our users.
Secure desktop clients support same features as webmail client
Automatic synchronization for your encrypted mailbox
Your encrypted mailbox is automatically synchronized between the desktop client, the webmail client and the Androidand iOS app. No matter where you manage your encrypted emails, your mailbox is updated instantly on all devices.
Short-cuts for ease of use
The new desktop clients support all short-cuts that you are used to from the webmail version. Simply press F1 (Fn+F1)to view all available short-cuts in any opened window.
Two-factor authentication
Tutanota supports 2FA (U2F & TOTP) to further secure your email login. We recommend that you use a hardware token(U2F) as U2F is the most secure form of two-factor authentication.
The beta desktop clients do not support U2F right now.The reason is a known issue with WebAuthN that we plan to fix in the coming months.
Security features that make Tutanota stand out from the crowd
By making sure that all your data is always end-to-end encrypted, only you own your data.
On top of the built-in encryption, Tutanota's secure password reset andinnovative search on encrypted data are just two important features that make surethat no third party - not even we - cangain access to your data.
Here are the most important features that make Tutanota's security unrivaled:
Mac Encrypt Pdf
- end-to-end encrypted mailbox
- end-to-end encrypted address book
- automatic end-to-end encrypted emails between users
- end-to-end encrypted emails to any email address with a shared password
- secure password reset that gives us absolutely no access
- full-text search of encrypted data executed locally
- TLS with support of PFS, DMARC, DKIM, DNSSEC, MTA-STS
- open source code for the entire client as well as Android & iOS apps
Tutanota combines security with ease-of-use
Tutanota is the secure email service that combines the advantages of the cloud – availability, automatic back-up,auto-sync, cost-efficiency – with the advantages of hosting your emails on your local server – security and data sovereignty.
Stop using email services that don't respect your privacy!Learn here how you benefit from going Premium for only €1 per month.
Get started now and pick your favorite Tutanota email applications to use an encrypted mailbox easily on all yourdevices:
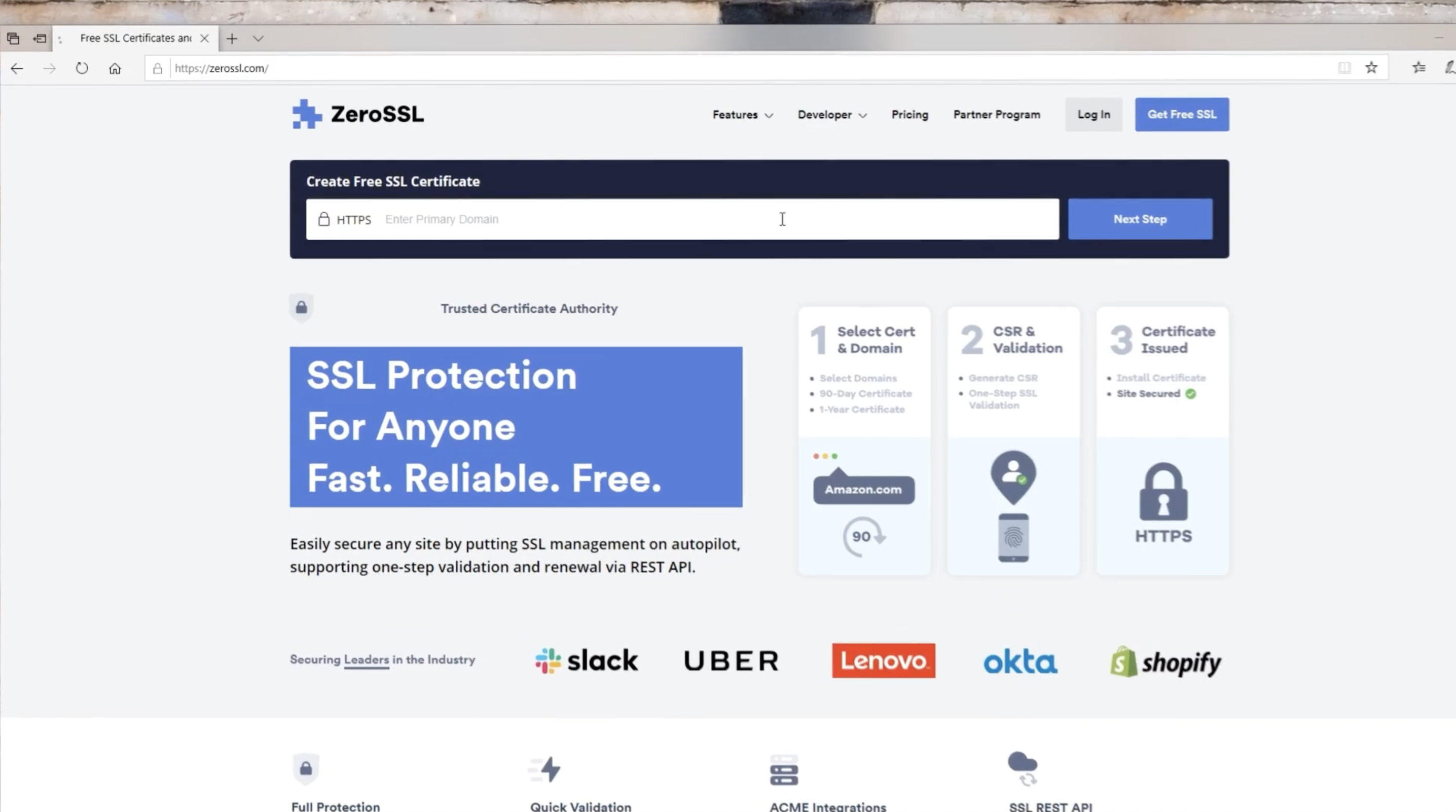
I will describe here how I did to set up HTTPS with a free SSL certificate issued by Let’s Encrypt. We will use Porunov Java ACME Client (PJAC): a Java CLI management agent designed for manual certificate management utilizing the Automatic Certificate Management Environment (ACME) protocol (example here: https://github.com/porunov/acme_client/wiki/Get-a-wildcard-certificate).
Use OpenSSL command lines or another GUI tool for keystores.
I am really bad at remembering openssl commands and options. Instead I feel more comfortable with tools like xca (https://hohnstaedt.de/xca) to generate key pairs, CSR and to display certificates.
Let’s start with generating 2 key pairs: one for Let’s Encrypt account and another one for the actual server (note I have used 4096 bits keys).
Next, we will generate a CSR for the server key pair. The important field is Subject Alternative Name in case of wildcard certificate.
The 2 key pairs and CSR must be exported so we can use them in PJAC command lines.
Let’s Encrypt is our Certification Authority.
First, register:
Then request order:
Files are created in digests folder, we will use them to update our domain.
Mac Client For Lets Encrypted
The previous commands have created two files in output folder pjac/digests (parameter –dns-digest-dir). We have now to update our domain’s CNAME using the generated strings so to prove we actually are in control of our domain (the so called DNS challenge).
Two TXT DNS records must be created, one for each of the digest file:
This can require some minutes to propagate. The next step of verification will depend on actual completion of this update.
If everything is alright, our domain is now authorized and we should be able to generate and download certificate:
We are done with the certificates, they are available in pjac/certdir:
If we import then in our xca keystore the full chain certificate, this is what we should see:
Let's Encrypt Client Windows
Note that Let’s Encrypt delivers 90-days-valid certificates only: this is on purpose as the philosophy is to improve security by renewing certificates more often, and in an automated way.
Change SSL server’s certificate of our ABAP AS
The following explanation may not be that useful in practical case: most of the time your SAP Gateway will be behind a web dispatcher, high availability load balancer or any kind of reverse proxy and your SSL certificate will be set up in this internet front facing server only.
Anyway, the interesting point is that the following shows that we don’t need to bother with sapgenpse any more and we can manage our keystore independently using openssl for instance.
Now that our signed certificate is loaded into our xca keystore, let’s export it together with its private key in PKCS12 format in order to use it in our ABAP AS. You have to set and remember the export password.
We can head to STRUST in ABAP AS to update our certificate. STRUST is not really the easiest and most understandable transaction, so here are my hints:
- left tree view shows all expected or actual PSEs
- right pane shows the selected PSE (the one you have selected in left tree)
- in left tree, “File” is not really a PSE but a tool to load external PSE
Steps:
Encrypt Mac Disk
- Switch to “Change mode” and double-click on “File” in the left pane
- In the “Open” popup, select the .p12 file we have exported earlier from xca, then provide the password we set during export
- SAP will complain about missing certificate in the chain. They must be downloaded from https://letsencrypt.org/certificates/, you will need to download “Let’s Encrypt Authority X3 (IdenTrust cross-signed)” and “DST Root CA X3”. Import them one by one as requested by popup message.
- Once loaded, right pane shows the certificate signed by Let’s Encrypt
- Now in top left menu File > Save as, choose SSL server DFAULT
We are done, in left pane SSL server standard > System wide : light should be green, and a double-click on your system should show the new certificate.
Depending of your version of Netweaver, your newly uploaded certificate may be active right away or you may need to restart your server in ICM.
Try to connect to your server (Fiori launchpad) and check the green lock in the toolbar: if you display details of the certificate, you should find your expected certificate as signed by Let’s Encrypt:
Every 3 months you will need to renew your certificate: this means you repeat steps from “Request order from Let’s encrypt”.
With Let’s encrypt, this is now easy to get free certificates that you can use in your own custom environment (like your own S/4 in your home cloud). This is especially convenient whenever you want to expose some API and consume it from an external application, as you will not face the security warnings about your self-signed certificates any more.
